What is Thotcon?
Thotcon is an information security convention that takes place yearly in Chicago. Its name comes from the
312(th-o-t) area code for Chicago. This conference had a number of different talks in two different tracks, so you always had a choice of what to do at any given time. Beside the talks were the villages, where there were
many booths setup with different activities including ham radio, a capture the flag challenge, lock picking,
and retro gaming. A lot of these infosec conferences feature hardware badges. Besides being an indicator
that you paid to attend the event, these badges are often programmable and serve as piece of electronic
artwork to remember the event by.
The event badge for Thotcon 0xA.
 |
The Badge
The badge features an ESP32 system on a chip microcontroller and is overall very similar to the ESP32 “Thing”
by Sparkfun. It features a speaker near the bottom of the badge (see above), a microphone, 5 capacitive buttons, and 6 LEDS.
The back of the Thotcon 0xA badge.
 |
The provided firmware on the badge was a puzzle challenge for all Thotcon attendees. I didn’t get too far into the challenge, but I managed to get the badge to play a message coded in the NATO phonetic alphabet after pressing the right combination of values.
Besides the puzzle challenge was a challenge for the best badge hack. I would have liked to participate in this if I had come with a group, but I decided to wait until Thotcon was over before making something with the badge to allow myself the time to attend more talks. I plan on adding a project made with the badge to my personal page when I get around to it.
Lockpicking
I spent about 40 minutes at the lockpicking station where they had all different types of locks to practice on. I had never attempted to pick a lock before and I was very surprised at how easy it was
to pick many of the locks.
I mostly used a rake pick and half diamond pick. These picks aren’t meant to be used to pick individual pins. Instead they are meant to “scrub” or “rake” the pins in an effort to push all of them up. This is as opposed
to a method called “single pin picking” which is when a gently curved pick is used to push up individual pins.
Double and triple peaked rake picks.
 |
Half diamond pick.[1]
 |
There were a few locks that were much more difficult than the rest. They were protected from the “rake”
and “scrub” methods of lockpicking by having special pins with notches. These notches
would stop the barrel from being turned when the pins were pushed to the wrong height.
This station was very enjoyable. Picking locks with the techniques I was using was very meditative. I found
was able to do it even while having a conversation with someone. It evokes a similar feeling to using one of the
“fidget” devices that recently gained popularity.
Takeaways from the Talks
Rob Rehr gave a talk about badge hacking and adding on to existing badges. He explained how there was a movement to create a standard for adding onto badges by using the “Shitty Add-On” standard which allows for expansion using I2C. This standard uses four pins in a square consisting of 3.3V, GND, SDA, and SCL.
The shitty add-on standard. Explained.[2]
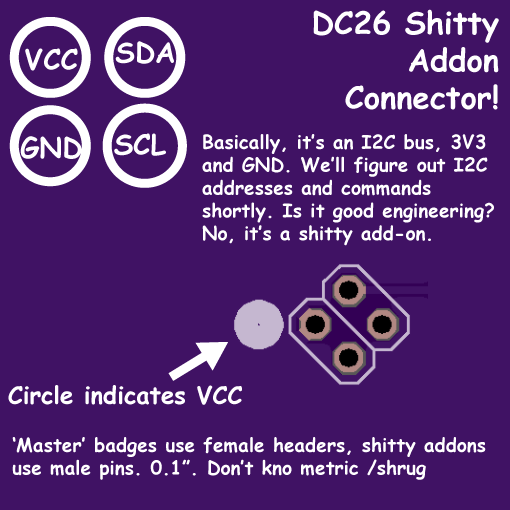 |
He also talked about at device he designed called the SAOGenie which is used as a “man in the middle” to read data sent via the I2C bus and repeat the data via UART. The device is designed specifically for the aforementioned “Shitty Add-On” connector.
Two members, RiotDoge and B_Meson, from a left wing, alternative, media collective called Unicorn Riot gave a talk called “Open Source Intelligence Techniques for Monitoring the Alt-Right Online”. This talk was mostly about how they expose dangerous people who hide behind online anonymity. This process involves infiltrating a Discord, Slack, or other chat server used by a hate group to collect information from its users. They can then report the server to the hosting company and release the chat logs online. Using every scrap of information they collect, a lead can be followed using other social media like Facebook to connect an anonymous identity to a real one. They heavily recommended a book by Michael Bazzell called Open Source Intelligence Techniques: Resources for Searching and Analyzing Online Information, saying they reference it often in their work.
During the Q&A someone asked about the types of people they are targeting. They stated it was for the most part people connected to violence, but overall it is on a case by case basis.
Conclusion
Thotcon 0xA was my first infosec conference and I had great time attending the event. I hope to go to many more in the future. I learned about a lot of new things that I look forward to exploring and I am very excited to make a project with the badge.
1
“Lock Pick - Half Diamond - Small.” Amazon.co.uk: DIY & Tools, Walker Locksmiths, www.amazon.co.uk/Lock-pick-half-diamond-small/dp/B008B8MTJI. Link
2
Benchoff. “Shitty Add-Ons.” Hackaday.io, www.hackaday.io/project/52950-shitty-add-ons. Link